Making cybersecurity elementary [Q&A]
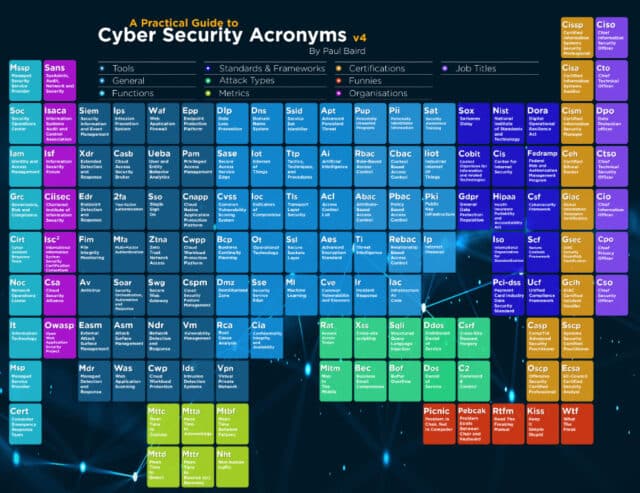
There are so many terms and acronyms used in the cybersecurity sector that it can be a little overwhelming at times, even for people who work in the industry.
Paul Baird, director of cyber security operations and engineering at Advanced Software and fellow at the Chartered Institute of Information Security (CIISec) has produced a round up of all the terms that you might ever need to know in the security space in a format based on the periodic table of elements.
We talked to him to learn what he wants to achieve with this and why it's so important to address gaps in cybersecurity knowledge.
BN: What led you to create the Cyber Security Elements chart, and to update it?
PB: The original idea for the document was based around my sons doing their cyber security degrees and the many questions on acronyms I was getting from them. I realized that if they were struggling, there must be others out there having the same issues.
Why a periodic table design? I remembered back to my school days and realized how useful the layout was in chemistry so started the design along those lines.
I have had so much interest in this -- it has been translated into multiple languages and shared by thousands of people -- that I have realized that, as much as it is fun for me to create and support this, there is demand for this kind of learning aid. I want to keep updating this as new and forgotten acronyms are sent to me.
I released the latest version alongside last year's CyberScotland Week, and I presented this at Morgan Stanley while sharing insights on the less technical aspects of cybersecurity. This format is about making it easy for people to understand all the different elements and changes going on in security right now.
BN: What problems do you think IT and security professionals face at the moment?
PB: There has been a huge shift in the IT security industry away from traditional IT and how we secured it through to today’s vast digital landscape with mobile devices, operational technology, cloud and other new developments. It's like the shift from the old castle and moat security analogy where you just had to keep the bad guys out, through to today's hybrid landscape where you have to think about security on multiple levels and areas.
Security today is more about planning the environment and understanding how people will work, so you have to look at the future and multiple perspectives. Alongside managing risk, you also have to look at the business impact and how to translate best practices so that they support how people live and work.
Cloud is a big area of change -- some of the traditional rules that were possible to enforce around security are no longer applicable, and there are huge changes in how all these applications and digital services are put together. Modern applications running in the cloud or using Kubernetes require some different approaches to keep them secure, and that has developed into its own specific best practices around where to get the data you need to check that you are secure over time.
Securing cloud deployments can also be easier -- you have more data coming at you from your deployments and can see what they are up to. The challenge here is not that you don’t have enough data to secure things, instead you can have too much data coming at you. It can be harder to see the wood for the trees.
BN: What have you added to the chart this time around -- anything that IT security pros should look out for?
PB: There are a few new acronyms that are entering the market -- for example, cloud security posture management (CSPM) covers how well you understand your cloud deployment or deployments, and what your approach to security translates to those systems. This is one of those markets that is starting to expand. Alongside this, external attack surface management (EASM) is one that I think a lot of security professionals could get value from. You want to understand what attackers might see, and any potential routes into your network that you may have overlooked.
The other main additions this time around are the organizations in the security space that support us all in learning and sharing best practices, and a set of acronyms that are popular in the security sector. My particular favorite of those is where you have a PICNIC issue -- Problem In Chair, Not In Computer -- however, while it might be funny to point the finger at end users that cause problems, it also reminds us that so many of the problems that exist around security are human, not technical. We have to make security easier for everyone, not just on the management side, but for employees too.
BN: What are the best areas to concentrate on if you want to make improvements to your security?
PB: The first step I always ask companies to make is around their asset management. Do you have an accurate list of all the assets that your company has? If not, you need to build one and quickly. Is that list accurate, and how much detail can you get? Many companies compile an asset register, but they then don't keep that list current, so they are looking at and making decisions based on out of date information.
This list can help you understand the size of the problem that you have. At the same time, it can be demoralizing if you have a list of thousands of vulnerabilities that all need to be patched, so your next step should be to prioritize where you need to put your efforts. This is not just about filtering for the assets that you have, or looking at CVE data, but at what systems are most important to your business and need the most protection. Prioritizing those critical applications first can help you keep those assets secure, and then you can look at automation to help patch and secure secondary systems.
BN: How can you help yourself and your team to improve security without burning out?
PB: Aside from getting the right tools in place, it's important to know your team and how they respond to pressure. Security is a stressful career -- Gartner predicts that half of cyber security leaders will change jobs in the next two years, and a quarter are planning to move into completely different roles instead. So, any work that you can do to improve your team’s efficiency will have a direct impact on how you can retain staff and keep them feeling that they are making a difference.
Preventing burnout in your team involves understanding them as people, how they work, their personalities and goals, and then keeping in touch with them on a regular basis. With the pandemic resulting in more remote work, security teams faced more pressure to keep operations running and at the same time, they possibly had less contact with their peers. This isolation may have led to more people feeling the pressure and burning out. So, putting the right processes in place to help you and your team keep in touch, be there for each other, and be more efficient in your work can all help keep control over stress.
Alongside looking at the people aspect, consider how you can make more use of automation. For example, can you improve your patching with automated deployment? While there are some critical patches that might need to be fully tested, others can be scheduled and deployed automatically to clear up potential issues without needing as much human intervention. This approach can improve your success rate in deploying updates while also helping you concentrate on where your team can make the most difference.
BN: Any other guidance that this chart can help with?
PB: I think the biggest thing for security is how to help other people in the business understand what it is we do. The sheer number of stories around major brands getting hit has put IT security on the radar for boards and for CEOs, so they know they have to do something. They know that they spend money on security. But the issue is how to explain what 'good' looks like to that audience. For example, how does a good patch management or asset inventory approach translate into good business security.
Learning how to speak the language of risk, not IT security, will help. Putting it in terms around risk can help business leaders understand IT security better. At the same time, it fits alongside new cyber insurance policies and how to reduce the impact around potential attacks. Providing boards with simple metrics -- "this is what good looks like, and this is how we match that" -- is where there is the biggest opportunity to improve security and reduce risk.
Image credit: Paul Baird